-
Category
تطويري
-
Presence
0 SAR
-
online
600 SAR
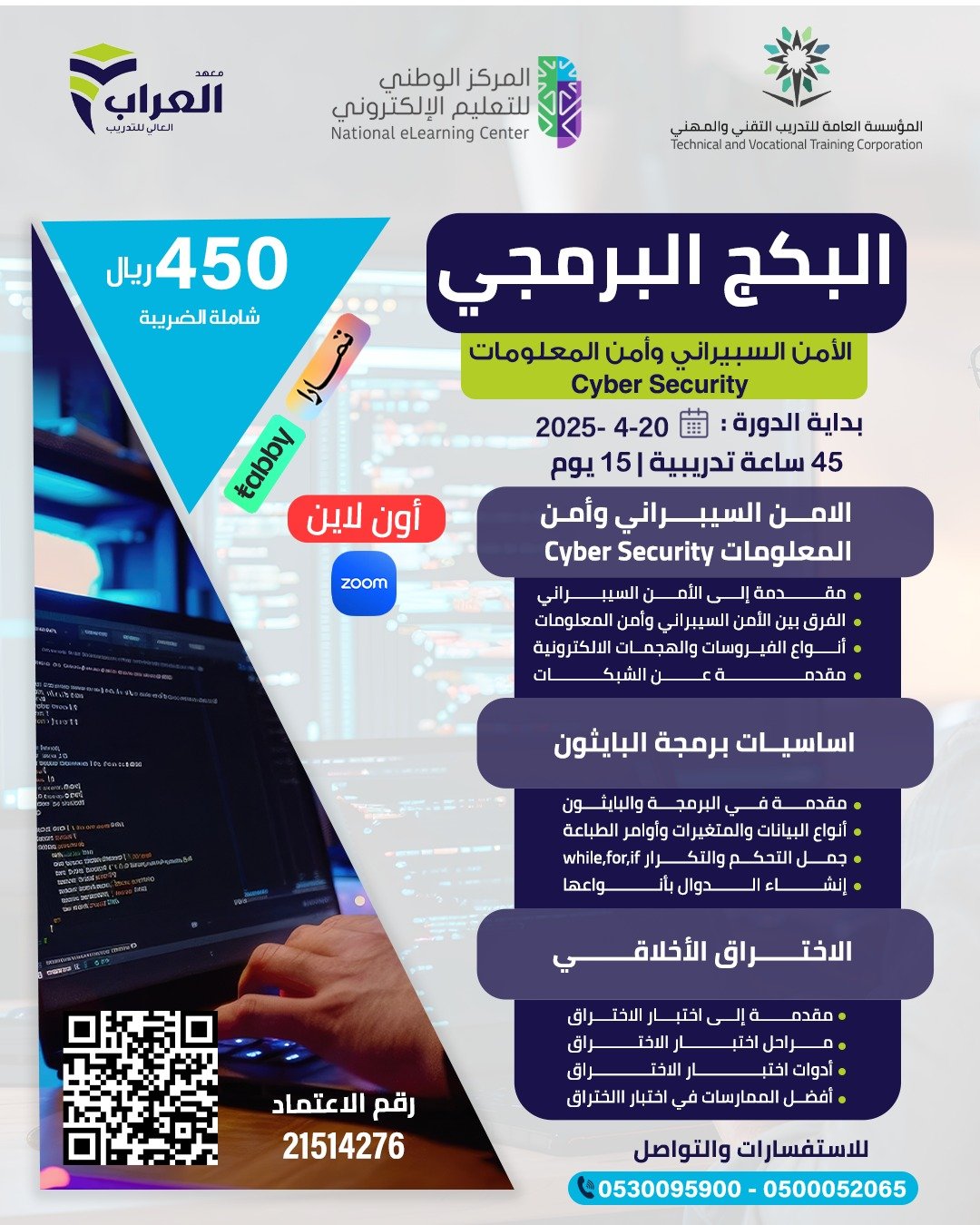
Online
600 ريال
Cyber Security and Information Security
This program aims to provide participants with basic knowledge and develop their skills, strategic capabilities and the competitive position of their establishments.
Details
Training Program Description (Training Course)
This program describes the threats facing cyberspace and methods of protection against them. You will be able to understand the basic principles of encryption, how users are exploited to obtain sensitive data or gain unauthorized access, and other related topics.
General Objective of the Training Program
This program aims to train participants to understand the rules, foundations, and elements of cybersecurity, as well as the various threats facing information system users working in different industrial, economic, and sensitive institutions. It also clarifies the legal aspects and pillars of cybersecurity protection and explains the nature of ethical penetration testing. Furthermore, it outlines international efforts to protect countries and vital institutions from cyberattacks, and trains participants on cybersecurity principles and how to manage information systems in critical institutions related to national security, as well as industrial and vital institutions.
Detailed Objectives of the Training Program
1. To understand ethical penetration testing and the difference between penetration testing and vulnerability assessment.
2. To understand the purpose of conducting penetration testing, its types, and testing methods.
3. To gain a thorough understanding of the steps for downloading and installing Virtual Machine and Kali Linux.
4. To understand the process of reconnaissance and information gathering, and reconnaissance methods.
5. To understand security vulnerabilities and the most prominent of these vulnerabilities.
6. To understand the history, policies, dimensions, and concept of cybersecurity.
7. To understand the characteristics of cybersecurity, including security and confidentiality solutions.
8. To understand cyber risks, including cybercrime, its types, and the nature of cyberattacks.
9. To understand the motivations behind countries' interest in cybersecurity.
10. To gain a thorough understanding of countries' efforts in the field of cybersecurity.
11. To understand the requirements of cybersecurity.
12. To understand the concept of cyber deterrence and its requirements.
13. To understand cybersecurity strategies.
14. To understand the role of legislation and laws in cybercrimes.
15. To understand the impact of legislation. Laws in curbing cybercrime
16. Understanding the concept of cyber piracy, its causes and manifestations
17. Understanding the concept of operating systems, network security, and how to implement information security
18. Understanding cyber extortion, its penalties, and its effects
Course information
- Course start date : 2025-05-13
- Duration : 30
- Hours: 45
- Number of seats: 1000
- studying days : from الأحد to الخميس
- Study time : 09:00 - 12:00
- Training period: صباحي
- training type: حضوري

 EN
EN AR
AR
